The Important Attributes of Managed IT Solutions That Can Change Your Organization's Technology Facilities
In today's significantly intricate electronic atmosphere, companies have to consider how managed IT solutions can serve as a catalyst for technical transformation. Scalable infrastructure administration and constant technical assistance give the agility required to browse varying demands.
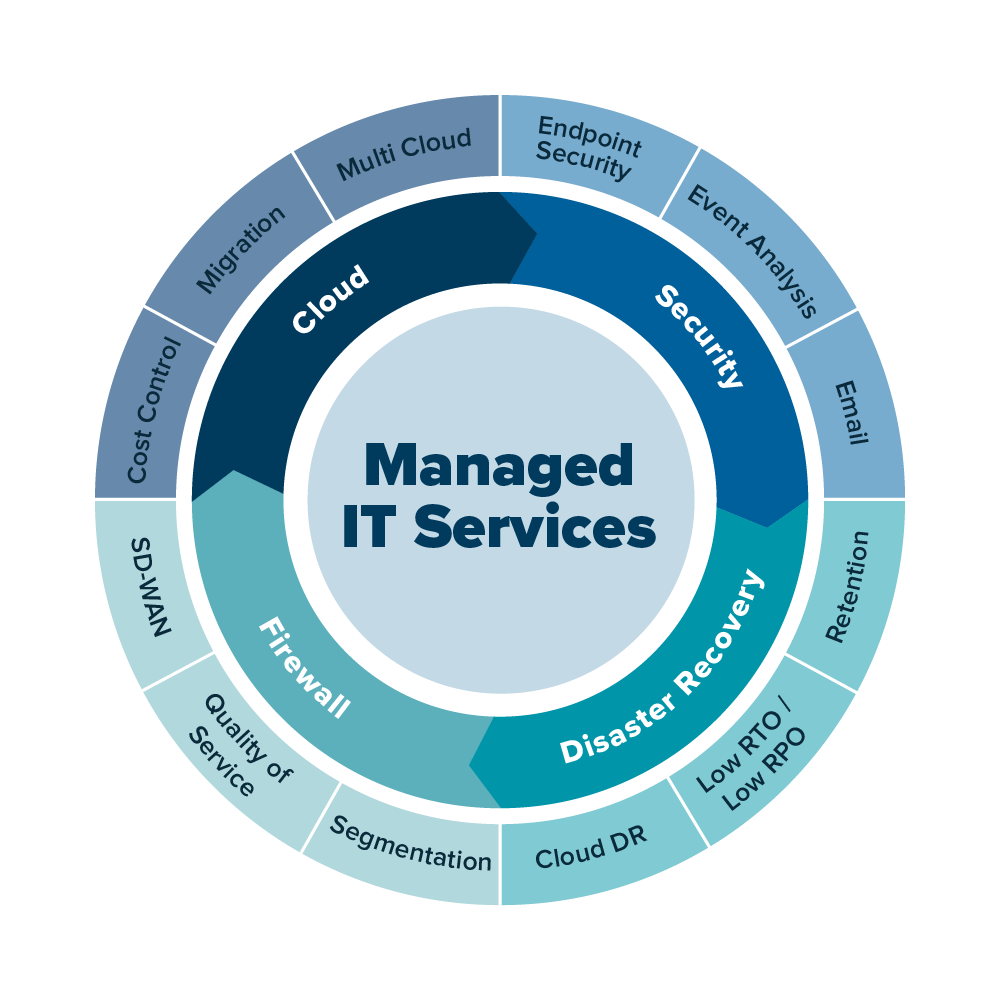
Proactive Network Surveillance
In today's progressively electronic landscape, efficient positive network surveillance is necessary for maintaining optimum IT performance and safety. This approach involves continuous oversight of network activities to recognize and address prospective problems prior to they escalate into considerable issues. AI Integration. By leveraging sophisticated surveillance tools and technologies, organizations can get real-time insights into their network performance, ensuring that resources are utilized efficiently and downtime is lessened
Aggressive network keeping an eye on includes numerous functions, consisting of performance evaluation, web traffic surveillance, and mistake discovery. By methodically analyzing network website traffic patterns, IT groups can pinpoint anomalies that might indicate security violations or efficiency bottlenecks. Additionally, this forward-thinking approach permits the timely application of spots and updates, reducing vulnerabilities that might be exploited by destructive actors.
Additionally, proactive tracking fosters a society of constant renovation. Organizations can refine their IT processes by examining historic data and patterns, enabling them to anticipate future requirements and scale their facilities accordingly. Eventually, buying aggressive network checking not just boosts functional effectiveness however likewise enhances the total resilience of a company's technology infrastructure, creating a more secure and durable environment for its electronic operations.
Comprehensive Cybersecurity Solutions
Aggressive network checking acts as the structure for comprehensive cybersecurity services, making it possible for companies to protect their digital properties against an ever-evolving threat landscape. By continually evaluating network web traffic and system tasks, organizations can detect abnormalities and possible threats before they intensify into substantial breaches.
Comprehensive cybersecurity solutions incorporate numerous layers of defense, consisting of advanced danger detection, case reaction, and vulnerability monitoring. With the assimilation of expert system and artificial intelligence, these services can recognize patterns a measure of cyber dangers, permitting speedy treatment. Regular security audits and assessments are important elements, ensuring that vulnerabilities are identified and remediated without delay.
Moreover, worker training and recognition are crucial in enhancing the human element of cybersecurity. By enlightening team on finest techniques and possible threats, companies can develop a society of security that decreases dangers.
Information file encryption and protected accessibility controls additionally play important duties in safeguarding delicate details, ensuring that just accredited employees can access important systems. Ultimately, detailed cybersecurity remedies empower organizations to keep the integrity, confidentiality, and schedule of their data, fostering trust with customers and stakeholders while sustaining business connection in a progressively digital world.
Scalable Infrastructure Management
Reliable management of IT infrastructure is essential for companies intending to adapt to varying needs and maintain functional effectiveness. Scalable facilities management allows companies to respond promptly to development or contraction in workload, making sure that resources are straightened with present demands. This flexibility is necessary in today's vibrant market, where modifications can take place quickly.
A vital element of scalable facilities management is the capability to stipulation resources on-demand. Organizations can take advantage of cloud computing remedies that permit the seamless addition or decrease of calculating power, storage space, and networking capabilities. This not just boosts performance but additionally optimizes costs by ensuring that companies pay only for the resources they make use of.
Moreover, automated tracking and administration devices play a crucial function in preserving scalability. These devices provide understandings into use patterns, making it possible for companies to forecast future requirements accurately and adjust sources proactively.
Eventually, scalable infrastructure administration promotes resilience, allowing companies to browse market variations while lessening downtime - AI Developers. Managed IT services. By buying a versatile IT structure, businesses can boost their pop over to these guys operational agility and position themselves for sustained development in an ever-evolving technical landscape

24/7 Technical Support
As organizations increasingly count on innovation to drive operations, the value of durable technical support ends up being critical. Reliable technological support is not simply a responsive solution; it is an aggressive element of IT monitoring that guarantees systems work efficiently and successfully. Organizations take advantage of 24/7 schedule, allowing issues to be settled quickly, lessening downtime, and preserving performance.
Handled IT services offer a dedicated support team furnished with the know-how to attend to a range of technical difficulties. This includes troubleshooting hardware and software application problems, settling network connection troubles, and offering individual assistance. With a concentrate on fast response times, services can expect very little disturbance to operations.
Furthermore, a well-structured technological assistance system includes numerous interaction networks, consisting of phone, email, and live conversation, guaranteeing customers can reach out for assistance in their recommended way. Routine training and updates for the support team better guarantee they remain present with technological innovations and emerging risks.
Ultimately, comprehensive technological support is a cornerstone of managed IT services, making it possible for companies to utilize modern technology successfully while concentrating on their core company purposes. AI Integration. This strategic financial investment not only improves functional performance but likewise promotes a culture of technology and durability
Information Back-up and Healing
How can services guard their critical information versus loss or corruption? Carrying out a durable data back-up and healing method is necessary for companies intending to protect their very useful details. Handled IT solutions offer comprehensive solutions to ensure that information is continually backed up and can be rapidly recovered in the occasion of an unanticipated occurrence, such as hardware failing, cyberattacks, or all-natural disasters.
A well-structured data backup strategy includes normal evaluations of data criticality, establishing the frequency of back-ups, and selecting in between complete, incremental, or differential backup methods (Managed IT services). Cloud-based remedies provide scalable storage space alternatives, allowing organizations to store big quantities of information securely while supplying very easy access for healing
Furthermore, a dependable recuperation plan involves testing back-up systems regularly to ensure that data can be brought back precisely and quickly. This minimizes downtime and reduces the effect on service operations.
Conclusion